 Just another persistent Twitter XSS Just another persistent Twitter XSS
Written by DPMonday, 19 July 2010*UPDATED 20 Jul 2010 : 10:39pm* - A mirror of the now corrected vulnerability has been published. Also, read on an excellent technical blog post by Billy (BK) Rios about another Twitter XSS bug...
-
Romanian security researcher "d3v1l" from Security-Sh3ll, has notified us just a few minutes ago about a persistent cross-site scripting (XSS) vulnerability that he discovered on Twitter's help center. He has already tweeted about it too:
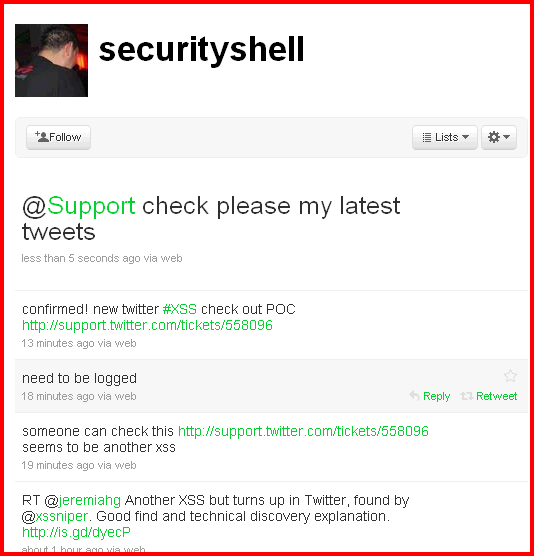
This is the second Twitter persistent XSS reported within a month and requires the victim to log in the account. More specifically, the simple XSS attack vector works due to improper input validation of a parameter within the "comment-body" section of the help center:
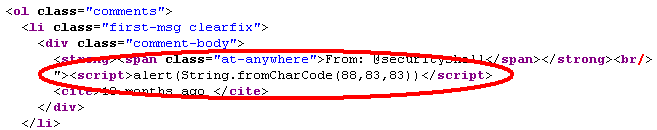
Millions of Twitter users are exposed to potentially malicious attacks that degrade their privacy and security levels; and Twitter has not yet corrected the issue nor was aware about it - maybe all help center web pages have successfully passed the code security review process or such a process never existed, who knows? They know! :)
It is only a matter of few minutes or hours before they apply a code "patch".
Screenshot of persistent Twitter XSS:
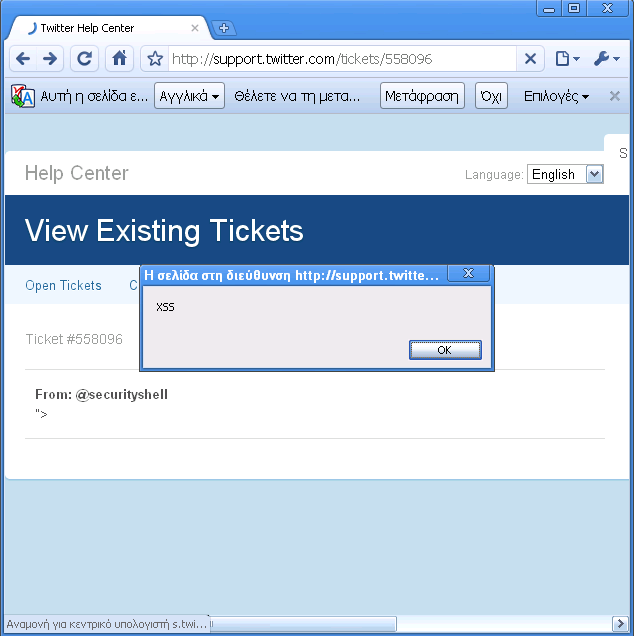
Twitter Related News on XSSed:
"Persistent XSS vulnerability affecting Twitter promptly corrected" - 27 Jun 2010 - DP
"17-year-old promoted his website on Twitter with harmless XSS worm" - 15 Apr 2009 - DP
| 